Wifi Router Setup Guide
Where Does this IP Take Me?
IP that you enter into the web browser is the IP address of the router. A router has many services such as ssh and FTP running. When a certain application (such as ssh) tries to connect with a particular device, they use the well-known port number for that particular application (22 for ssh) along with the IP of the device they want to connect to.
When you enter the default IP of the router on the web browser, the browser will send the HTTP request to the router on port 80 or 443.
When the request is received in the router on the above ports, a tiny web server running will handle this request. The response is the web page that we see.
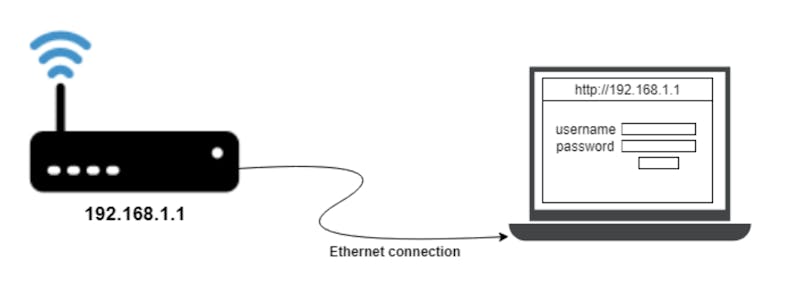
This is similar to how every website works, the google.com we enter is translated to an IP which is handled by the webserver located in some location. The only difference in the web logins is the webserver is running inside the router and the IP is the private one.
As an example, if we consider a wifi router running Openwrt operating system, the webserver that it uses for web login is uHTTPd. uHTTPd is specifically developed to be very compact and less resource-hungry because the routers have less processing power and memory constraints. Every vendor has its own lightweight web servers which are mostly proprietary.
Why So Many Different IP Addresses?
Different vendors tend to have different default IP addresses and most of them are starting with either 192.168.x.x or 10.x.x.x. Here’s why.
All the IPs we have internal to our network are called private addresses, it is not unique in the world, you can have 192.168.1.2 IP in your home and your neighbor can use the same IP without a problem in their network. The allowed range of IP addresses for private use are the following:
10.0.0.0 - 10.255.255.255
172.16.0.0 - 172.31.255.255
192.168.0.0 - 192.168.255.255
Manufacturers can use any address from the above IP address range in their routers for providing their network. Some manufacturers go with 192.168.x.x series and some 10.x.x.x series. They typically have the first IP of that range assigned to the router. For the rest of the network, the IP is provided from a DHCP server dynamically in the same subnet address as the router’s.
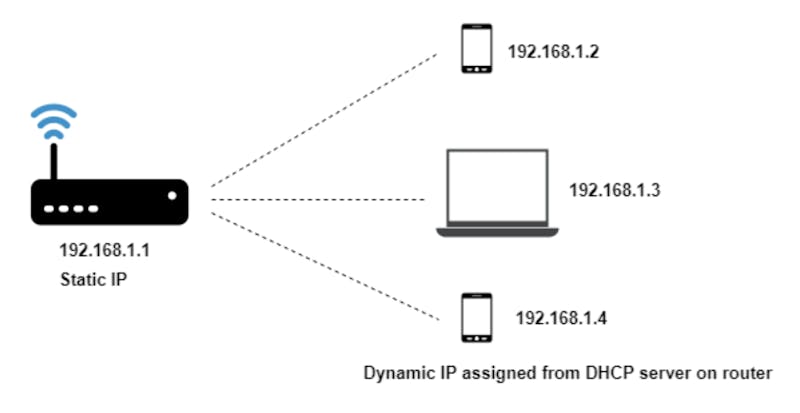
If your router’s default IP is 192.168.1.1 your devices in your network will probably have IPs in the range 192.168.1.2 to 192.168.1.244.
In the earlier days, private addresses were divided into classes and each class had a different number of hosts they could handle, for example, the IP addresses starting with 10.x.x.x were class A, and they could handle up to 16777214 hosts, which is a huge number for even a small scale company. The 172 series could handle up to 16384 hosts. And the 192.168.x.x up to 254 hosts.
From the above three classes of private addresses available the class C - 192.168.x.x was the most sensible one for home use, since 254 hosts is more than sufficient for home use. With the introduction of CIDR (Classless Inter-Domain Routing), we could create blocks of IP with a number of hosts that we want; But most home routers still stick with the IP of 192.168.x.x. (192.168.1.1, 192.168.1.100, 192.168.0.1, etc),
Apart from using IPs, vendors also have the URLs to login to the router, for example in the case of TP-Link it is http://tplinkwifi.net. These URLs are internally translated to the default IP.
Login Credentials and Security
If you had bought a router a few years back and looked into the login information, you’d see fairly simple login information such as:
Or something that’s similar like admin, 1234; the password was meant to be changed during the setup process. But there are many devices in the wild with default logins.
Having default logins is a serious security issue. Websites like shodan.io let users scan the routers on the internet with default logins; In fact, it is one of the top searched thing after webcams and netcames. once you know the make and the model of the router anyone with access to this information can log in into your router. This leaves the router prone to malware and many attacks.
Username: admin
Password: admin
Manufacturers have come up with solutions that are more secure than the fixed login credentials such as unique default login passwords for each device, shipping devices without any password and make password setting mandatory during the setup process.
There have been instances where the manufactures failed to provide a secure login password trying to provide a unique password. One example is from TP-Link, which was shipping their WR702N devices with the login password extracted from the MAC address of the router, which might look safe in the first look until you realize that the MAC addresses are broadcasted in every packet and can be easily obtained by anyone in the physical coverage area of the access point. So it’s always better to change the default passwords even though the login information is unique.
Next time you look at router web logins, I hope you see things differently and always remember to change your default password!